IAST (Interactive Application Security Testing)
What is IAST?
Interactive Application Security Testing (IAST) is a security testing methodology that combines the aspects of Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). IAST tests applications in real-time during their execution to identify security vulnerabilities more effectively.
To fully understand IAST, it’s important to first understand SAST and DAST.
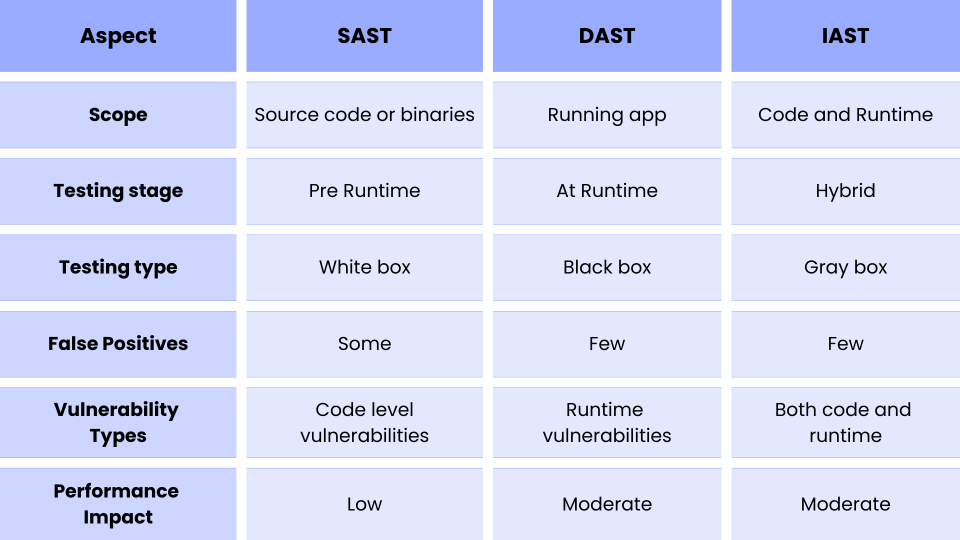
- SAST: SAST is a methodology for analyzing source code, byte code, or binary code to identify vulnerabilities in software applications. The limitation of this SAST methodology is that it tests the application at the code level, not actually running the application.
- DAST: DAST addresses the limitations of SAST up to some level by providing a dynamic approach to testing applications. In this approach, the application is tested while it is running. However, it does not check the application from the code level. That is the limitation of DAST.
- IAST overcomes the limitations of both SAST and DAST by combining their strengths. It analyzes the application both at the code level and during execution. By monitoring the application in real-time as it runs, IAST can identify a wide range of vulnerabilities like SQL injections, XSS, authentication issues, sensitive data exposure, etc. This approach provides more accurate and comprehensive security testing and insights into how the code behaves during execution.
Why is IAST a Grey Box Testing Method?
As you know, IAST is a combination of SAST and DAST. SAST is a white box testing method where the tester can go through the application code and do the testing. On the other hand, DAST is a black box testing method since it won’t check the code level and tests how the running application behaves.
Since IAST combines these methods, it has black box and white box testing features, making it a grey box testing method.
Difference Between SAST, DAST, and IASTAdvantages of IAST
- Real-time analysis: Most IAST tools come with IDE integrations, leading to real-time code analysis. The security analysis will then happen while the application is in development.
- Detailed vulnerability insights: IAST tools follow a developer-friendly approach by broadly describing the related vulnerabilities. It will start from the code level and continue to understand the context in which the vulnerability happened. Developers do not need to be security experts because it will provide detailed information on the vulnerability and remediation steps.
- Early detection of vulnerabilities: IAST provides a shift-left approach, where testing is conducted earlier in the Software Development Life Cycle. This approach allows you to address vulnerabilities before they become deeply embedded into the code base.
- Continuous monitoring and adaptability: IAST tools continuously monitor the application during the development, testing, and even production stages. This ensures that frequent changes to the application and the code base do not introduce new vulnerabilities.
- Wide Language and Framework support: Modern applications are most often a mix of languages and technologies. Therefore, security testing needs to be covered across the whole stack to be effective. IAST tools are designed to work across different environments, whether the application is built with Java, .NET, Python, or other languages and a range of frameworks like Spring, .NET, Ruby on Rails, Django, and more.
Challenges and Limitations
- Initial setup: The organization may have to put in significant time and resources to configure the IAST tools according to their specific architecture, languages, and application frameworks.
- Custom environment requirements: Since IAST operates inside the running application, it typically requires a test environment that is very close to the production environment. Setting up such an environment can be complex, especially for large applications or those with a high degree of customization.
- Industry standards compliance: Not all IAST tools can support the specific compliance requirements for industries such as health or finance, where strict security standards and audits are mandatory. Organizations have to make sure that their chosen IAST tool aligns with their regulatory obligations.
- Runtime-dependent analysis: IAST is very good at detecting vulnerabilities that can be visible during the execution of an application. Anyways, it may not be very effective against issues like deep architectural flaws or vulnerabilities in code that are not executed during testing.
- Dependency on test coverage: IAST accuracy significantly depends on the quality and degree of test cases available during runtime analysis. If testing does not cover all the possible execution paths or user interactions, then it will miss some vulnerabilities.
- Compatibility issues: While IAST tools support multiple programming languages and frameworks, they sometimes cannot work in any environment or require some additional configuration to adapt smoothly to certain development setups. This may become a problem for organizations using any niche or highly customized technologies.
[blog-subscribe]
Interactive Application Security Testing tools
There are many IAST software testing tools, and these are a few popular choices.
- Seeker by Synopsys: Provides real-time vulnerability detection and analysis.
- Contrast Community Edition: Provides instant feedback on security vulnerabilities by continuously analyzing applications.
- Invicti: Seamlessly integrates with CI/CD pipelines, offering robust, automated security testing.
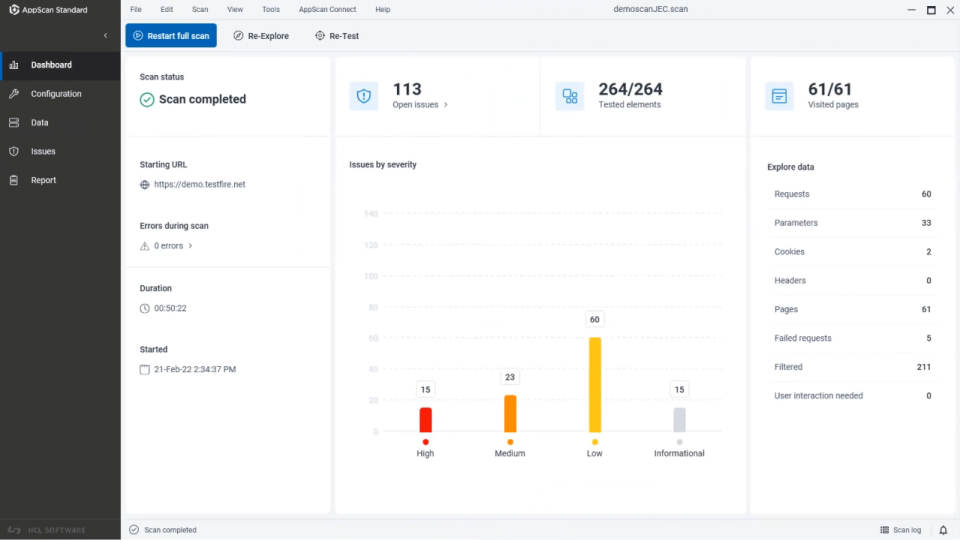
- HCL AppScan: Provides in-depth security testing by combining dynamic analysis with real-time monitoring.
- Checkmarx: Leverages deep code instrumentation to detect and report security flaws dynamically during runtime.
Conclusion
IAST combines the best of SAST and DAST to provide a comprehensive approach to application security. This hybrid methodology enables real-time vulnerability detection during code execution and offers detailed insights into vulnerabilities and remediation steps.
Although it comes with some challenges, such as initial setup complexity and dependency on test coverage, the benefits of continuous monitoring, detailed vulnerability insights, and broad language support make IAST an essential tool for modern application security.